Infrastructure managers and enterprise architects responsible for secure managed file transfer (MFT) face new pressures from throughout their organizations. For years, legacy MFT products have transformed custom-scripted transfer projects into scalable, reliable operations. But now, CISOs reeling from surging cyber-attacks mandate deeper defenses, and your Compliance Officer requires even more audits. Meanwhile, the business demands faster turnaround, and qualified staff is harder to find… and keep. Prevail over these challenges with managed file transfer designed from the ground up for simplicity, security, and governance. Easily deploy its virtual appliance cluster—or our hosted service—and configure your policies. Immediately benefit from the security of its hardened vault and built-in defense in depth. Configure trading partner workflows, start operations, and breathe a sigh of relief as your auditors and SOC now see every transaction detail in built-in audit reports, security analytics, and your SIEM.
Streamline and Secure Large-Scale File Transfer Operations
Secure MFT Server | Managed File Transfer
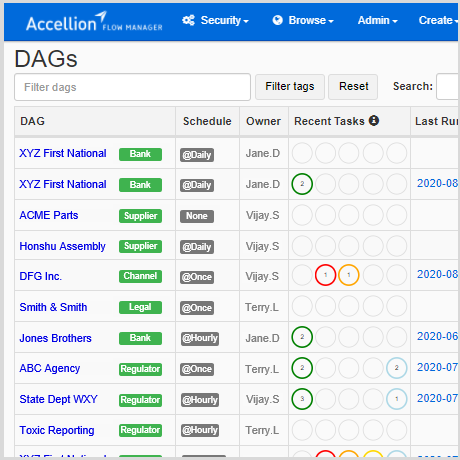
- Manage, monitor, and recover transfers with the Secure MFT Server’s graphical operations dashboard.
- Onboard new trading partners and author workflows simply and quickly.
- Trigger transfers with scheduling, polling, or events, or start them manually.
- Maximize end-to-end security with unique vault-to-vault transfers.
- Access data in folders, file shares, repositories, and cloud stores.
Automate Secure and Flexible Business Processes
Secure MFT Client | Managed File Transfer
- Make departmental file-based processes simple, foolproof, and compliant using the Secure MFT Client.
- Distribute throughout the organization, but manage centrally.
- Author visual workflows without coding.
- Leverage a library of two thousand connectors and workflow functions.
- Utilize content firewall functions.

Protect Your Content from Insiders and Advanced Threats
Hardened Virtual Appliance | Managed File Transfer
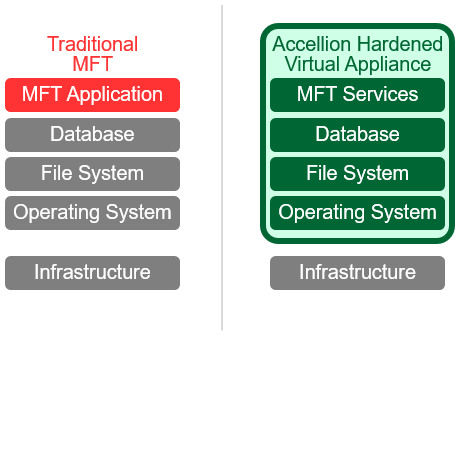
- The content firewall doesn’t just encrypt protocols and storage, it minimizes your attack surface by enclosing all system components in a hardened virtual appliance.
- It firewalls each server, defaults to most secure settings, shuts off unnecessary ports, removes unnecessary code, and isolates traffic between tiers.
- Accellion’s secure development lifecycle, regular penetration testing, and worldwide bounty program eliminate bugs before they become vulnerabilities.
- Like a smartphone, one button updates all the system components so you never miss a patch.
- Intrusion detection systems detect and alert on suspicious system modifications.