NEXT-GEN NAC FOR YOUR EVOLVING NETWORK
Secure Any IP-Enabled Devices, No Matter What.
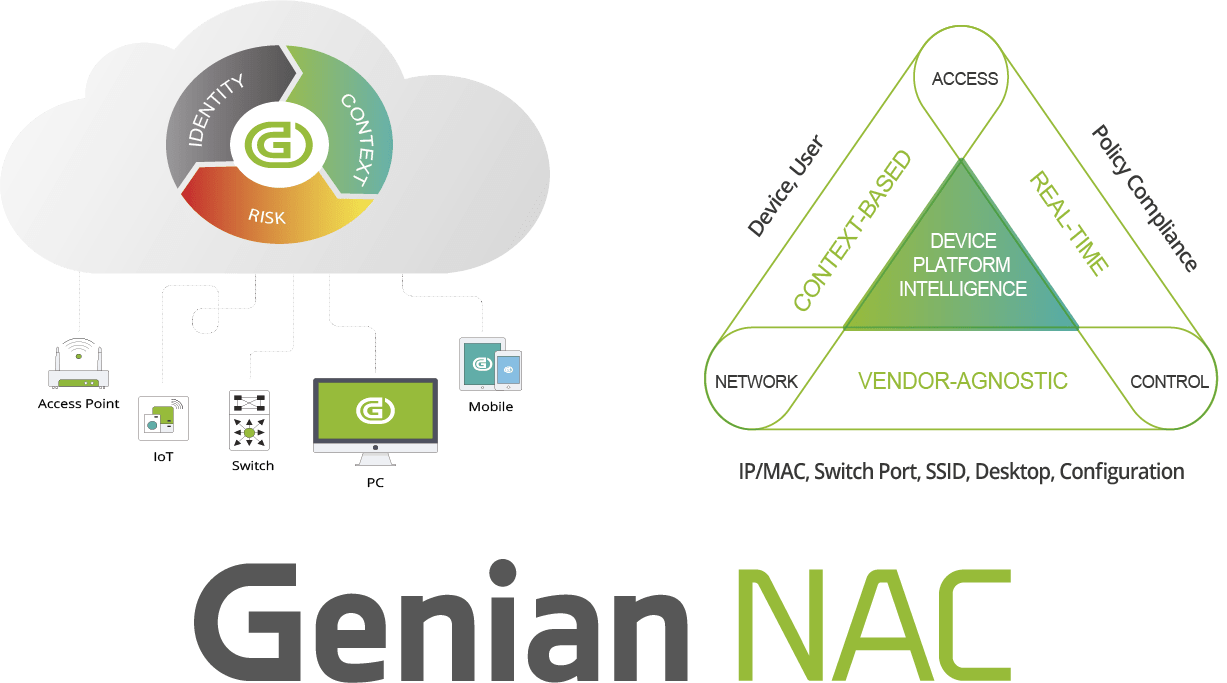
Genians’ Next-Gen NAC provides any organization with the most important cybersecurity features and functionality for keeping network assets safe and secure. Genians' Next-Gen NAC offers comprehensive network surveillance for all network-enabled devices and provides dynamic access control to preserve compliance with IT security standards without disrupting existing operations. It then uses automation to manage an organization's whole security portfolio in concert with NAC to provide a network access environment that is ideally secure.
Securing The Edge, Quickly & Accurately
Less Touch, Greater Results.
Essential NAC
Genians’ Next-Gen NAC provides any organization with the most critical cybersecurity capabilities and functions. These serve as a foundation for building a strong cybersecurity environment while also providing the most cost-effective pricing and implementation alternatives.
Actionable Compliance
In the real world, achieving cybersecurity entails going beyond any set of compliance requirements and taking the necessary actions that an active, real-time approach to security management necessitates.
Genian NAC supports practical security compliance by providing real-time network surveillance for all the assets in your network and ensures that are all compliant with your IT security policies. Without disturbing existing IT infrastructure or impacting systems availability, Genian NAC gathers and monitors the hardware and software asset information of all IP-enabled devices. It then leverages its Device Platform Intelligence capability to determine each device’s technical and business contextual details, identifies all known or potential device vulnerabilities, establishes the level of user access to be provided, and ensures that all detected devices are compliant.
Features
Non-Disruptive Sensing & Access Control At The Edge
Genians’ Next-Gen NAC provides any organization with the most essential cybersecurity features and functionalities to keep network assets safe and secure. Without disturbing existing operations, Genians’ Next-Gen NAC ensures full network surveillance for all network-enabled devices and provides dynamic access control to maintain compliance with IT security policies. It then leverages automation to orchestrate an organization’s entire security portfolio in concert with NAC to achieve an optimally secure network access environment.
Network Surveillance
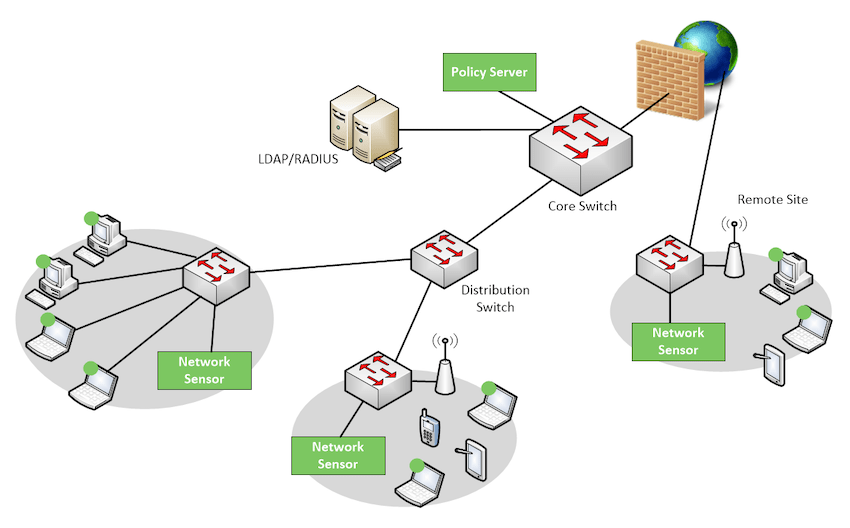
Genian NAC can monitor IP-enabled devices on your network in real-time using a non-disruptive Layer 2-based Network Sensor and classifies those devices and their users into logical groups based on your business requirements. Genian NAC has the intelligence to sort out a wide range of network-connected devices and their states to present immediate, meaningful, and actionable information.

Coverage
- Monitor heterogeneous network environments without changing existing network configuration
- Monitor wireless packets by Wireless Sensors or Agents
- Monitor all managed, unmanaged, and even legacy networking devices
Detection
- Provide the most accurate device platform information and see access trends
- Discover contextual access information (Who, What, Where, When, How)
- Detect compliance status change on time
Observation
- Find non-compliant, unknown, rogue, misconfigured devices
- Discover abnormal network traffics (e.g. ARP Spoofing/Bombing, MAC/IP Cloning, Port scanning, Invalid Gateway)
- Present personalized information through fully customizable dashboards
NAC
Genian NAC leverages multiple techniques to enforce IT security policies dynamically using contextual information (What, Who, When, Where, How) to quarantine any non-compliant devices and remediate them to be compliant through automated processes.
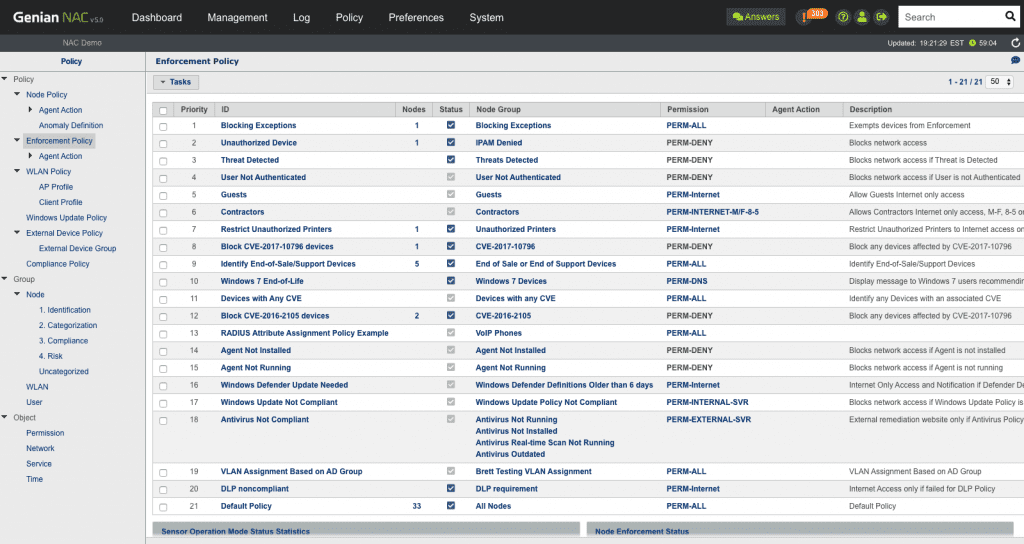
Dynamic Acess Control
- Condition-based grouping (Over 500 predefined conditions)
- Policy assignment based on the status change of endpoint compliance
- End-to-end access control inside of LAN
Multi-layered Access Control
- 802.1x: Built-in RADIUS server
- DHCP: Built-in DHCP server
- Layer 2: ARP Enforcement (using Network Sensor)
- Layer 3: TCP reset (using Mirror/SPAN Sensor)
- Layer 3: Inline Enforcement (Dual-homed Gateway)
- Agent: NIC/Power Control, Alert Popup
- Integration: Firewall, Switch port shutdown (SNMP, Webhook)
Genians: A Cybersecurity Leader in NAC and ZTNA Solutions
Genians, the NAC and ZTNA pioneer, clinches 4th spot in Gartner's "Market Share: Enterprise Network Equipment" report, affirming its stronghold in the cybersecurity realm. With 18 years of experience and 3,000+ global clients, Genians offers NAC-driven ZTNA solutions for seamless security.
In an industry that surged 24.3% YoY, Genians thrived by transforming traditional NAC and ZTNA into accessible, cost-effective, and efficient solutions for diverse sectors, including finance, education, healthcare, and government.
For those seeking simplified, powerful cybersecurity, visit us at www.genians.com – where industry-first solutions await. Experience the future of network security with Genians!
*Disclaimer: Gartner does not endorse any vendor, product, or service mentioned in its research publications. Genians is a leader in Network Access Control, providing security for organizations worldwide.
About Genians: Genians, listed as KOSDAQ: 263860, offers the industry's premier Network Access Control solution, securing millions of endpoints globally. Join us in building a more secure connected world by partnering with leaders worldwide.
Contact Us