IT Security And Compliance
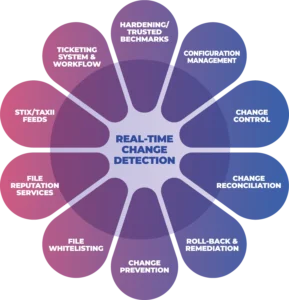
Next-Gen File Integrity Monitoring
What is File Integrity Monitoring (FIM)?
File Integrity Monitoring (FIM) is a category of cybersecurity technologies that monitors critical files and detects changes. While legacy tools were limited to monitoring system files, today's Next-Gen FIM tools can detect change to critical data wherever it exists, including:
- Windows Registry
- Drivers
- Installed Software
- Security Policies
- Services
- Network Share Files & Configuration
- Local Users / Groups
- Active Directory / LDAP
- Microsoft Exchange
- Network Devices (Firewalls, Switches, Routers)
- Hypervisors (ESXi, HyperV, XenServer)
- Databases (MSSQL, Oracle, MYSQL, Maria DB, IBM, DB2)
Why File Integrity Monitoring?
Organizations implement a File Integrity Monitoring solution for various reasons, like securing active directory and system files, data security, including zero-day attacks, and meeting the regulatory compliance standards or objectives with various regulations such as PCI-DSS, HIPAA, SOX, NERC, FFIEC, FISMA, GDPR, CMMC, CDM, SWIFT and more.
File Integrity Monitoring (FIM) is a crucial security practice that involves monitoring and analyzing changes to critical files on a system to detect and prevent unauthorized modifications or access. By regularly scanning and comparing the current state of files against their known, trusted baseline, FIM tools can quickly identify any unauthorized changes, such as tampering or malware infection, and alert security teams to take necessary actions.
FIM can be implemented using a variety of techniques, such as checksums, digital signatures, or behavior-based analysis, and can be performed on both on-premises and cloud-based systems. Additionally, FIM can provide compliance benefits by helping organizations demonstrate adherence to regulatory requirements, such as PCI DSS and HIPAA.
Overall, effective FIM is a critical component of a comprehensive cybersecurity strategy, and organizations of all sizes should consider implementing FIM solutions to protect their valuable data and systems from unauthorized access and modification.
File Integrity Monitoring Best Practices
Basic File Monitoring
- Lots of noisy alerts
- Uses a denylist to identify malicious changes
- Resource-intensive and relies on daily active scans
- "Shelfware" that's usually only present to satisfy compliance requirements
File and System Integrity Monitoring
- Cuts irrelevant change noise by 95%
- Uses denylists, allowlists, and trusted file registry to uncover malicious activity without swamping analysts with alerts
- Detects change in real-time and barely registers on the resource monitor
- Fundamental to maintaining real-time system integrity across corporate IT environments
Working From A Trusted Baseline

File Integrity in Real-time
CimTrak continuously monitors changes in real-time and responds instantly to unexpected/unwanted changes. Proactively prevent cyberattacks at the source without restricting operations to reactive threat feeds.

Complete Change Detail
CimTrak pinpoints exactly what has changed and provides complete change audit information. Forensic details provided with changes include; Who changed the information, What exactly changed, When it was changed, the process used to change it, and How.
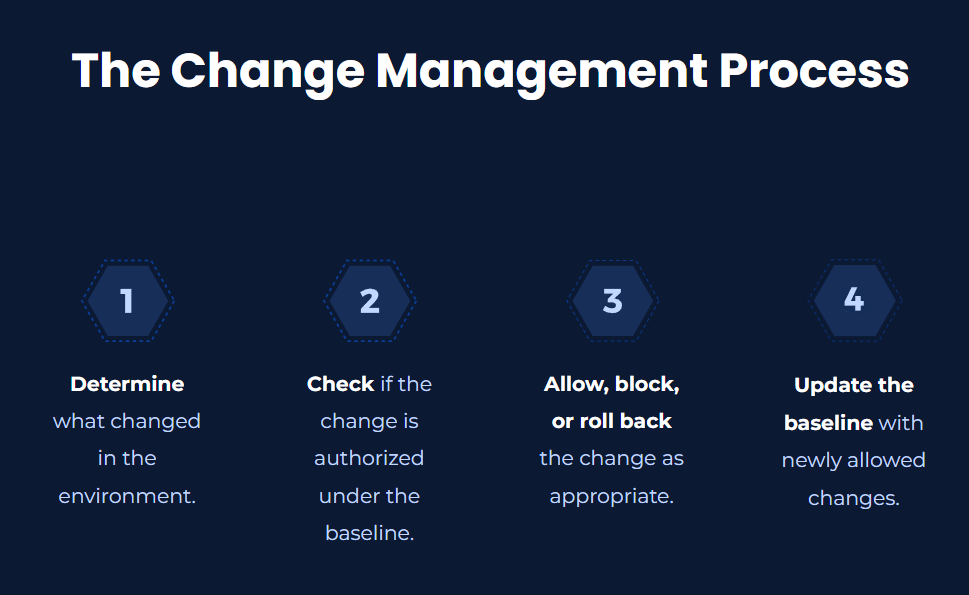
Change Management/ Change Control
CimTrak can pinpoint exactly what changed and provide complete change audit information. Knowing a change happened is of little use without understanding the corresponding metadata associated with the change.
Advanced file integrity monitoring (FIM) solutions like CimTrak give a deeper dive into unauthorized changes by not only letting you know exactly what changed but also other forensic details such as:
WHO changed the information, WHAT exactly changed, WHEN it was changed, and the process used to change it, and HOW.
System Integrity Assurance
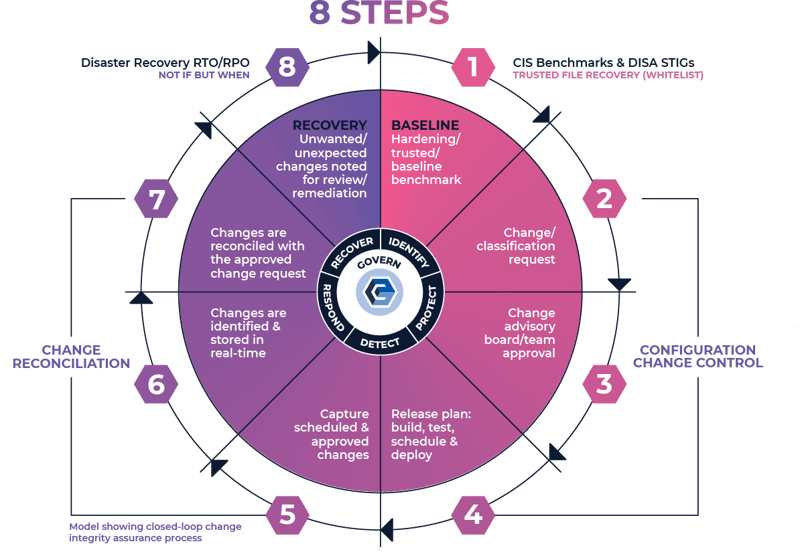
System Integrity Assurance (SIA) is the next evolution of FIM. It establishes a known, trusted, and authoritative baseline of what is allowed and then prevents, limits, or rolls back everything else. With true detection and response, whenever an unknown, unwanted, or unexpected change occurs, it’s managed by exception so that authorized changes are added to the baseline while malicious activity or unacceptable changes are highlighted for investigation and/or remediation.
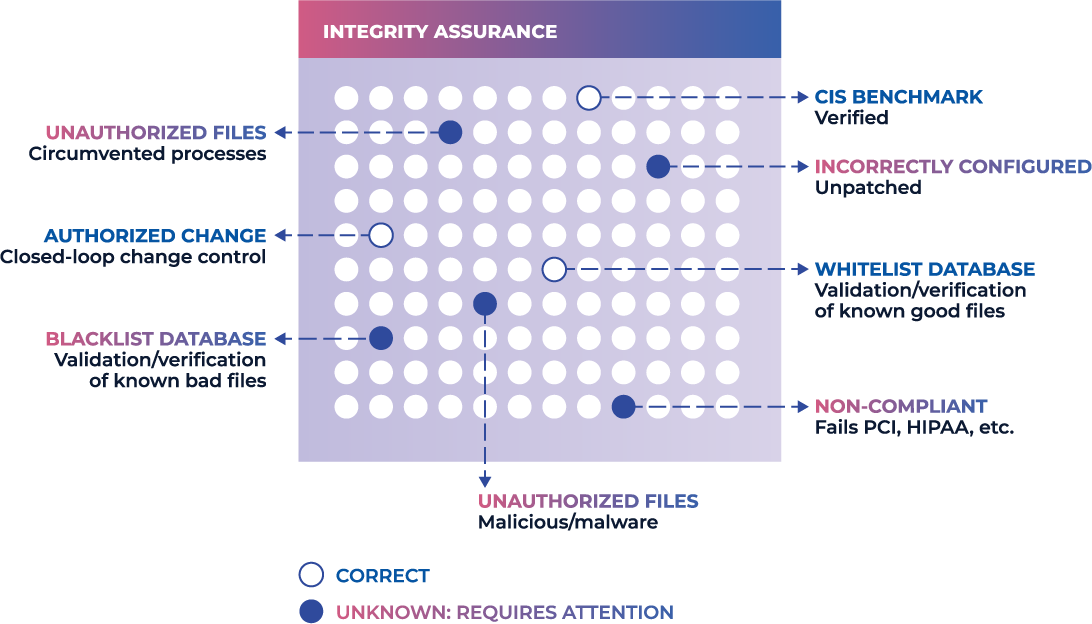
- True real-time change detection and response
- Integrated ticketing capabilities allow the classification of changes, maximizing security by focusing attention on the most critical changes
- Trusted File Registry™ service allows automatic reconciliation of known vendor updates and patches, resulting in significant time savings
SIEM Integration and More
CimTrak helps SIEMs do their job better by receiving system, application, and file change data directly from the file integrity monitoring tool itself.
This allows the SIEM to combine critical change information with other data streams, allowing for enhanced event analysis and correlation. Benefits include learning about security events more quickly and being able to provide better context surrounding those events. Alerts raised by a SIEM can be traced back to CimTrak, which can provide all of the forensic data (who, what, when, how) for the event, allowing for quick and simple root-cause analysis.
.png?width=622&height=198&name=Master%20Repository%20(1).png)
File Monitoring and Integrity Verification
in Real-Time
Legacy FIM tools lack real-time monitoring. This prevents organizations from responding to attacks for up to 24 hours, giving attackers time to cause damage, traverse the network, or steal data.
Next-Gen File Integrity Monitoring tools monitor for changes and verify file and data integrity in real-time. This provides two huge benefits:
Respond Instantly to Attacks
Known bad changes are prevented or rolled back automatically. E.g., if a configuration setting is changed out of compliance with CIS Benchmarks, the tool can instantly reverse the change.
Incident responders can triage unknown changes quickly without wasting time on "noisy" false positives.
Save Network Resources
Next-Gen tools scan the environment once to establish a baseline, then receive change data from agents and modules across the environment.
This process is highly efficient and barely registers on the resource monitor.
Next-Gen FIM Automates
Compliance and System Hardening
Compliance Automation
in 3 Easy Steps
A Next-Gen FIM tool automates compliance and system hardening by:
1. Building requirements of all applicable frameworks into the trusted baseline.
2. Continually monitoring all files and configurations against the baseline.
3. Raising alerts for issues or misconfiguration and providing clear evidence and guidance to resolve it.
How Next-Gen FIM Maps to
9 Compliance Frameworks
Next-Gen FIM can help your organization reach and maintain compliance with any framework. Just update your trusted baseline to include all relevant compliance requirements and then action a manageable number of alerts.