THIRD PARTY RISK INTELLIGENCE BUILT FROM A HACKER’S PERSPECTIVE
Black Kite fills a fundamental security gap by making it simple for businesses to non-invasively quantify and monitor cyber risk across thousands of third parties. We provide intelligence from a technical, financial and compliance perspective: eliminating false positives and ensuring a holistic approach to vendor risk management.
CYBER RATINGS PLATFORM
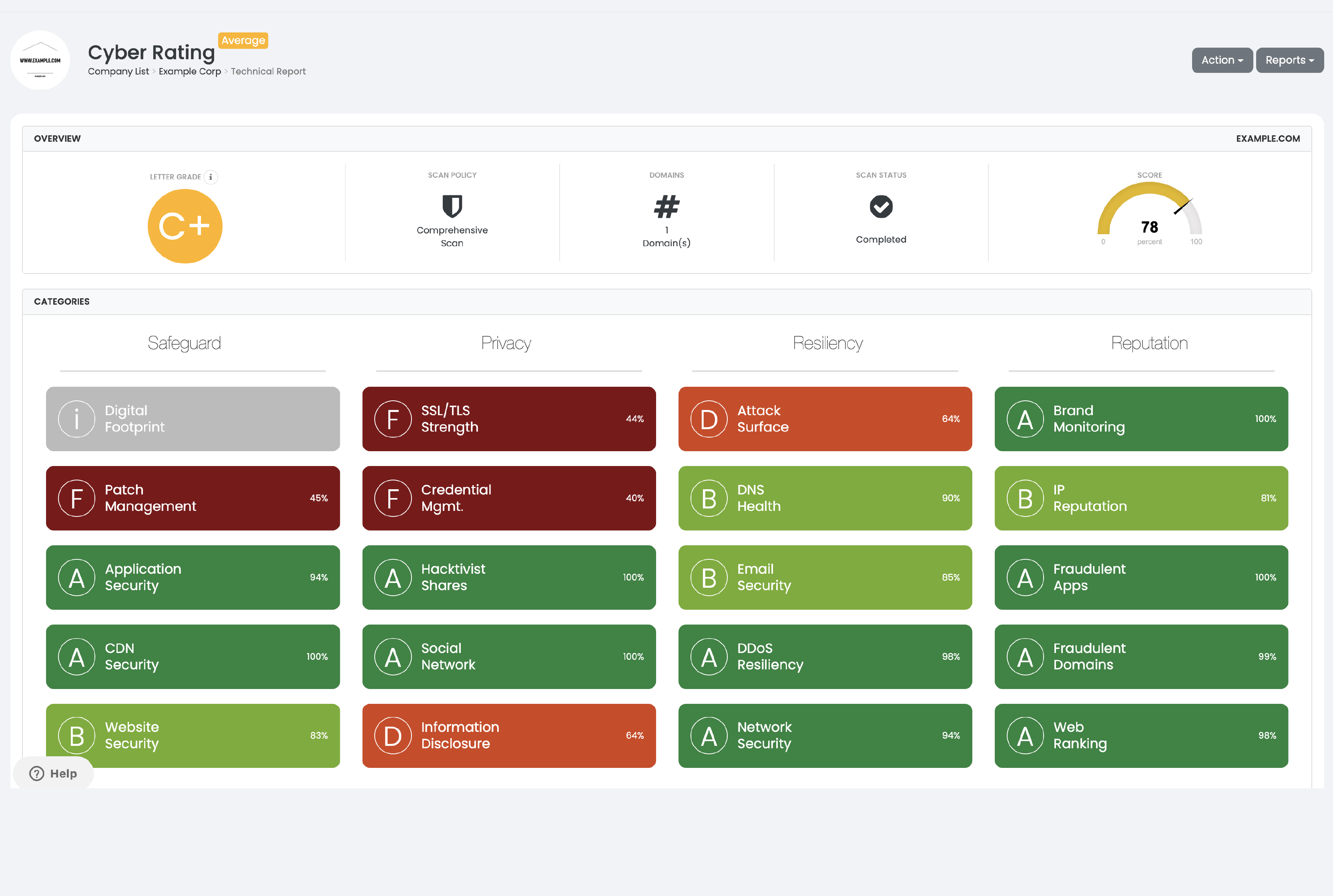
TECHNICAL CYBER RATING
Gain an easy-to-understand, trustworthy snapshot of your supply chain risk by visualizing defensible intelligence in the form of a letter grade. Black Kite utilizes industry-standard MITRE frameworks to convert technical data into digestible findings – allowing successful communication of risk to senior stakeholders
RISK QUANTIFICATION
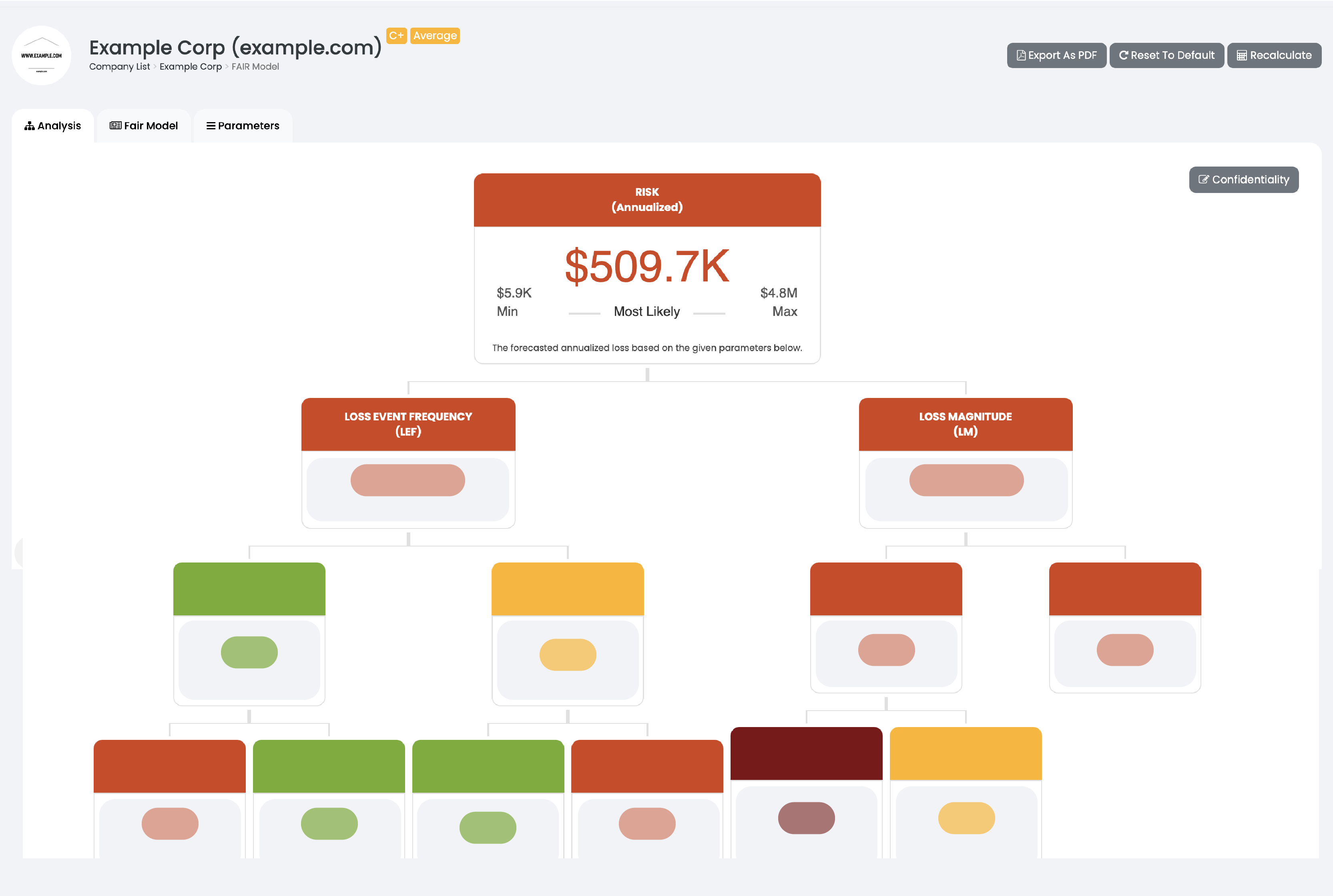
Black Kite uses the Open FAIR™ model to calculate the probable financial impact if a third-party vendor, partner, or supplier experiences a breach. Black Kite communicates this risk in quantitative, easy-to-understand business terms, facilitating a common language between IT and senior stakeholders.
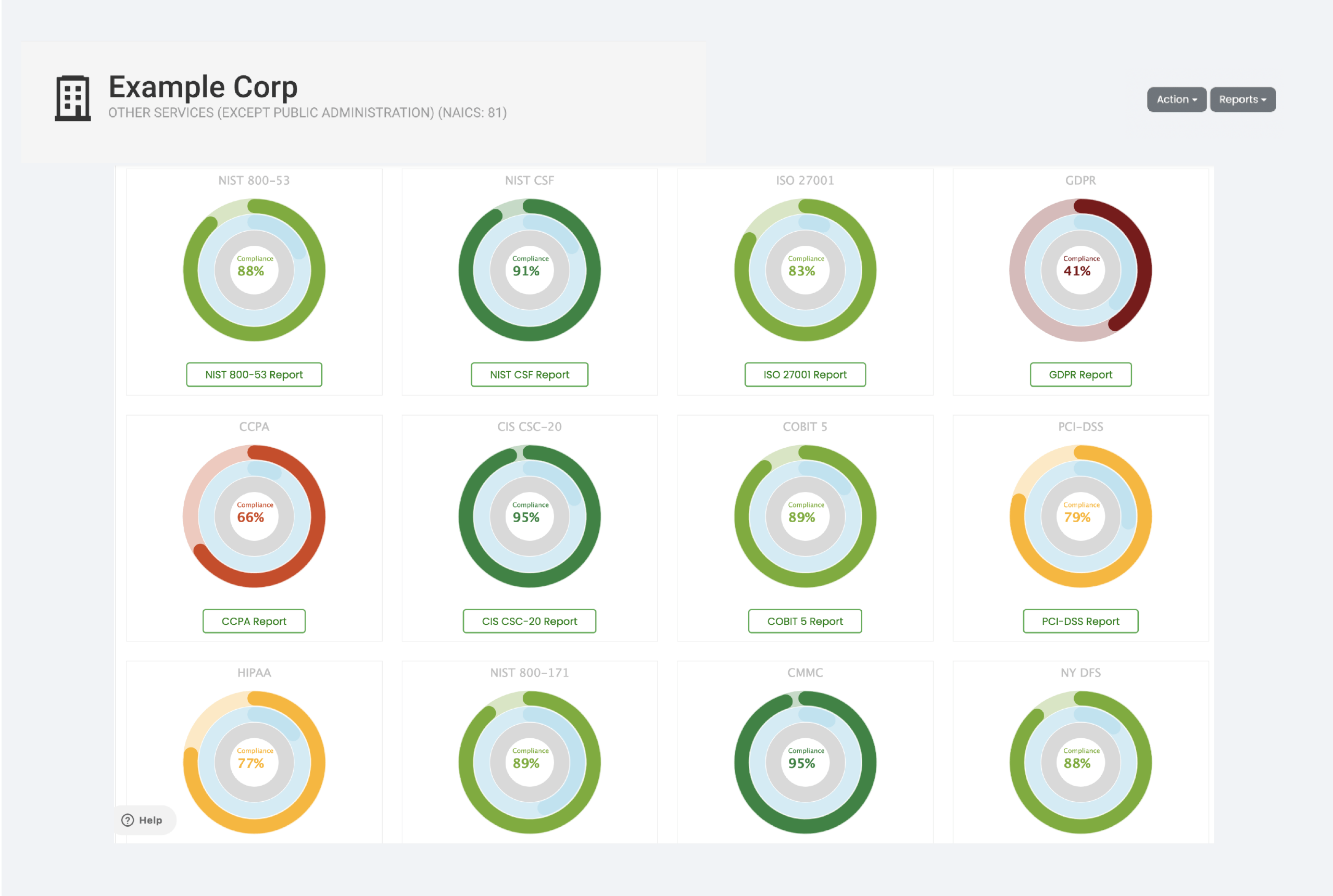
COMPLIANCE CORRELATION
Meet compliance requirements within hours, using automated parsing technology that maps to globally-recognized standards and frameworks with our UnIQue Parser. Additionally, the cross-correlation capability measures the external compliance level of a target company based on the standard input, saving time and effort for both you and your vendors.
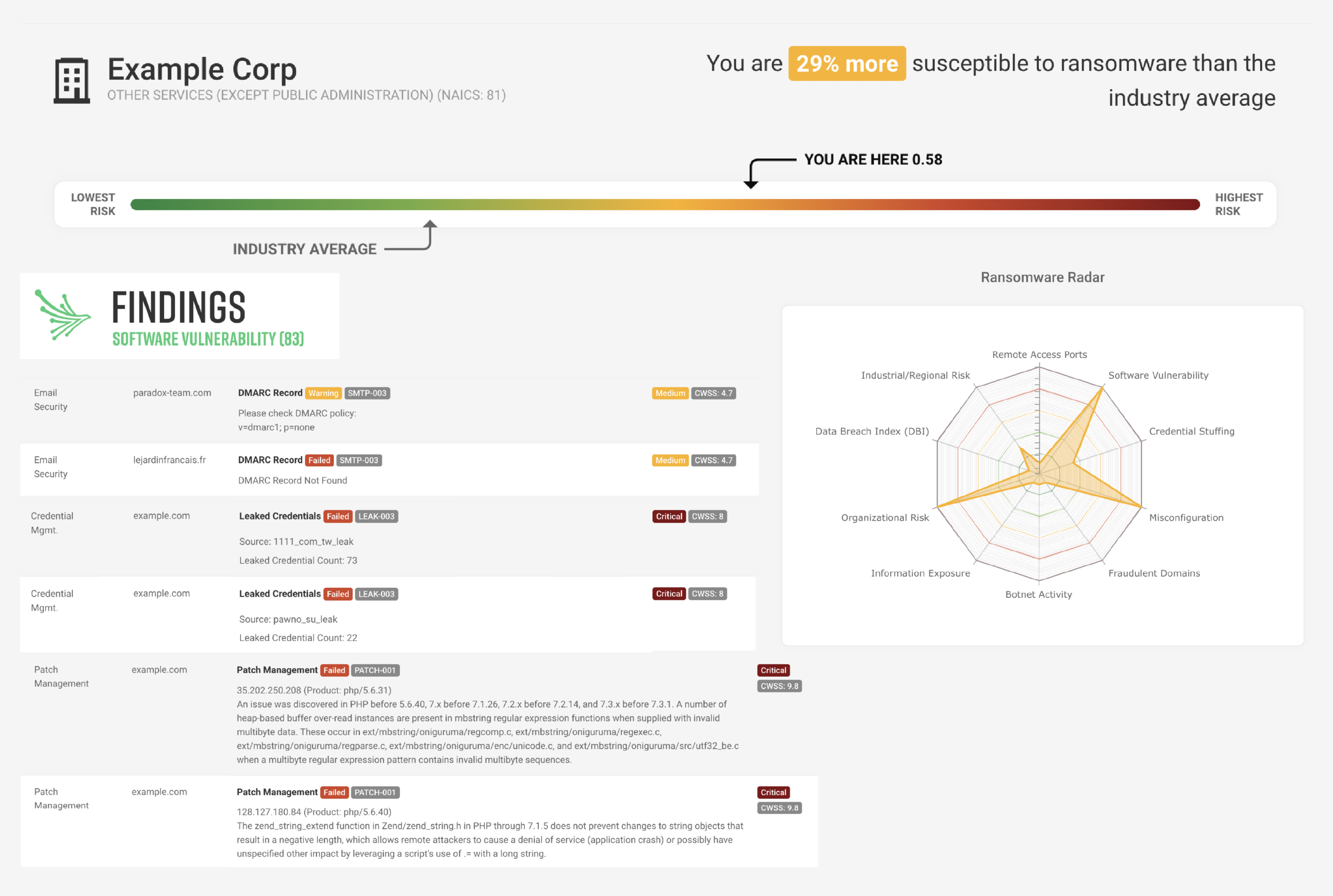
RANSOMWARE SUSCEPTIBILITY
The only cyber rating platform with a tool to detect the likelihood of a ransomware attack to your organization. The Ransomware Susceptibility Index® utilizes data analysis techniques and common indicators, including a third party’s location, industry, and annual revenue. By becoming aware of your risk, you can avoid business interruption and data loss by using our reliable data to develop informed policies around all emerging threats.
WHERE INSIGHT TAKES FLIGHT™
360° DEGREE VIEW OF CYBER RISK
Providing intelligence from a technical, financial and compliance perspective, Black Kite eliminates false positives and ensures a holistic approach to vendor risk management.
STANDARDS-BASED DATA
Black Kite is the world’s only fully transparent, standards-based cyber ratings platform, ensuring all users know exactly how their findings are calculated.
UNMATCHED SCALABILITY
Engineering the largest data lake in the world, Black Kite provides you with visibility into over 34 million companies and counting, with 20+ risk categories and 290 controls – 3x the competition.
Patch Management
Keep software on computers and network devices up to date and capable of resisting low-level cyber attacks. Criminal hackers can take advantage of known vulnerabilities in operating systems and third-party applications if they are not properly patched or updated.
Application Security
Security measures at the application level aim to prevent data or code within the app from being stolen or hijacked. Application security may include hardware, software, and procedures that identify or minimize security vulnerabilities.
CDN Security
Companies use content delivery networks (CDNs) — large distributed systems of servers deployed in multiple data centers across the Internet — for online libraries like JQuery. Detect vulnerabilities in services like edge caching, SSL offloading and edge routing.
Website Security
The main website of an organization is one of the most important assets. Detecting any code or server level vulnerabilities is crucial for a company’s reputation.
SSL/TLS Strength
The SSL/TLS protocol encrypts internet traffic of all types, making secure internet communication (and therefore internet commerce) possible.
Credential Management
When a website unintentionally reveals sensitive information to its users. Depending on the context, websites may leak all kinds of information to a potential attacker, such as usernames or financial information.
Hacktivist Shares
Hacktivism is the act of misusing a computer system or network for a socially or politically motivated reason. An example of hacktivism is denial of service attacks (DoS) which shut down a system to prevent customer access.
Social Network
Social media is part of a larger ecosystem of publicly available platforms that make up a new attack surface for threat actors to leverage.
Information Disclosure
When a website unintentionally reveals sensitive information to its users. Depending on the context, websites may leak all kinds of information to a potential attacker, such as usernames or financial information.
Attack Surface
The set of points on the boundary of a system, a system element, or an environment where an attacker can try to enter or extract data.
Digital Footprint
Your digital footprint refers to a digital collection of data that can be traced back to you. This includes IPs, domains, subdomains, email addresses and server fingerprints.
Email Security
Open-sourced techniques for protecting email accounts, content, and communication against unauthorized access, loss or compromise.
DDoS Resiliency
Detect malicious cyber-attacks that hackers or cybercriminals employ in order to make an online service, network resource or host machine unavailable to its intended users on the Internet.
Network Security
Analyze network-level problems and detect any critical ports, unprotected network devices, misconfigured firewalls, and service endpoints.
Brand Monitoring
A business analytics process that monitors various channels on the web or media to gain insight about the company, brand, and anything explicitly connected to cyberspace.
IP/Domain Reputation
Identify IP addresses that send unwanted requests. Using the IP reputation list you can identify if an IP address has a bad reputation or member of a botnet.
Fraudulent Applications
Fraudulent applications are used to hack/phish employee or customer data. This category identifies possible fraudulent or pirate mobile/desktop apps on Google Play, App Store, and pirate app stores.
Fraudulent Domains
Domains registered by fraudsters plan to launch phishing attacks, sell knock-off goods on spoofed sites, or use “typo-squatting” domains to make money off unintentional traffic for other sites.
Web Ranking
Cisco, Alexa and Majestic track web sites and rank them according to popularity, backlinks, and references. This subcategory shows trends, page speed test results, and Web Content Accessibility Guidelines (WCAG) 2.0 parsing compliance findings.