DeviceLock Stops Data Leaks at the Source
For any businesses in the modern economy, information used in corporate IT systems in the form of digital data has become a critical intangible asset for their growth, sustainability, and competitiveness. Such information includes intellectual property, customer data, company’s financials and trade secrets, PII and PHI of clients and employees, technology “know-how”, competitive intelligence, and many more types of meaningful knowledge. Data is very much “the blood” of corporate IT, and as a loss of blood is deadly dangerous for living organisms, so it is for businesses with leaks of data from the corporate environment and its users.
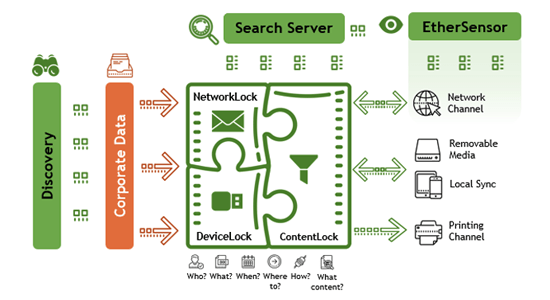
Protecting data is critical in today’s hyper-networked reality where ubiquitous mobile data communications, the Internet, social media, email, and other consumer applications, as well as the commercialization of cybercrime, have all combined to sharply increase the threats to IT security. The global pandemic of data breaches resulting from unauthorized access to, and dissemination of, valuable corporate information can lead to heavy financial losses from costly litigation, compliance fines by authorities, damage to reputation, and loss of revenue.

DeviceLock DLP leverages a lightweight enforcement agent that is installed on every protected computer and a central Group Policy MMC snap-in that is adjustable to any size and type of corporate network. There are also traditional central consoles that can be used for managing Macs, non-AD LDAP environments, and/or Windows workgroups. Running transparently for users and applications in the scope of normal business processes, DeviceLock Agents detect and prevent unauthorized data access and transfer operations on protected computers. The Agent’s multi-layered inspection and interception engine provides fine-grained control over a full range of data leakage pathways at the contextual level. For further confidence that no sensitive data is escaping, content analysis and filtering can be applied to endpoint data exchanges with removable media, printers, and PnP devices, as well as with the network protocols associated with connecting to Internet applications and services.
With DeviceLock DLP, security administrators can precisely match user rights to job functions with regard to transferring, receiving, and storing data on corporate computers. The resulting secure computing environment allows all legitimate users’ actions to proceed unimpeded while blocking any inadvertent or deliberate attempts to perform operations outside of preset rules.
Get in Touch with Us
We want to hear from you. Please feel free to email us at info@rasinfotech-dubai.com, or just speak your mind below. Please allow one business day to respond.