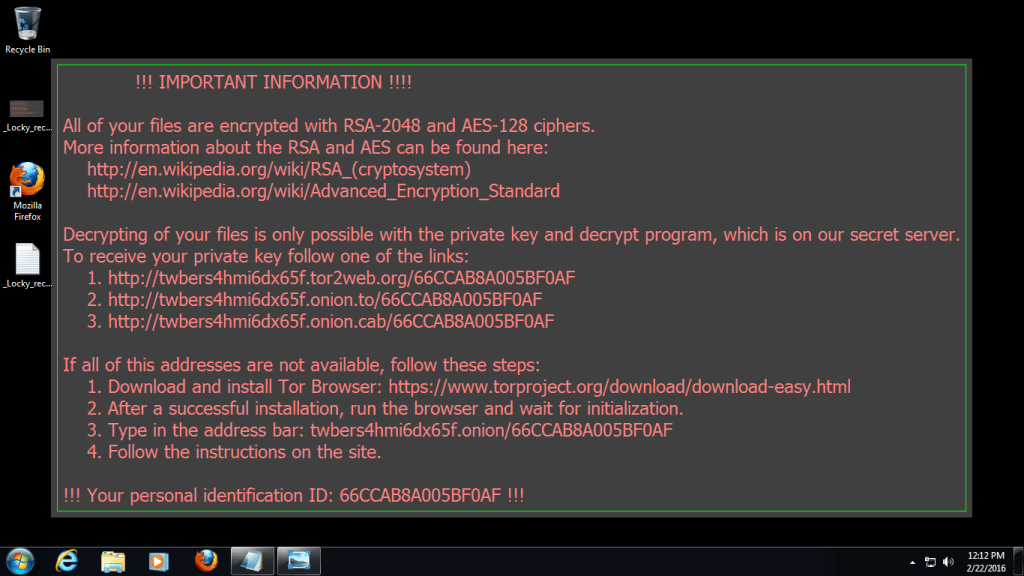
Over the past week, a new crypto-ransomware threat, dubbed “Locky”, has been making pretty big headlines.
So far, Locky’s most common infection vector has been via e-mail. A word document attachment is sent out claiming to be an invoice. When opened, the document appears scrambled and prompts the recipient to enable macros in order to view, and if they do so, an executable (ladybi.exe) gets dropped and starts encrypting data files using 128-bit AES encryption.
This particular campaign appears to be very well organized, with multiple localizations of the ransomware being deployed worldwide and a large, robust infrastructure in place to support it. Many reports have suggested that the actors behind the spam campaign that is currently spreading Locky are likely the same people who spread the Dridex banking trojan.
Locky auto-generates domain names to call home to. Forcepoint have detailed the domain generation algorithm.
If you’re running our software, DeepGuard, our behavioral detection engine, has been preventing both the attack vectors used by Locky and the behavior of the malware itself. These detections have been around for quite some time already. Following our tried-and-tested prevention strategy, DeepGuard notices malicious behavior, such as Office documents downloading content, dropping files, or running code. DeepGuard stops the mechanisms that allow these sorts of threats to infect your machine right at the source.
The following three detections block malicious behavior associated with Locky and its variants:
- Trojan-Dropper:W32/Agent.D!DeepGuard
- Trojan:W32/Pietso.A!DeepGuard
- Trojan:W32/TeslaCrypt.PE!DeepGuard
These three detections also protect our customers from Pony, Vawtrak, and the latest versions of TeslaCrypt.
Over the weekend, a new Locky infection vector surfaced. This infection vector involves a ZIP attachment containing a JavaScript file, that, if run, downloads the Locky executable and runs it. We detect that variant as Trojan-Downloader:JS/Dridex.W.
Source: https://labsblog.f-secure.com/2016/02/22/locky-clearly-bad-behavior/







Thanks for the good article, I hope you continue to work as well.Спаситель на продажу
I was extremely pleased to discover this page. I want to to thank you for ones time due to this wonderful read!! I definitely appreciated every part of it and I have you bookmarked to look at new information on your web site.
I was excited to discover this website. I want to to thank you for your time for this wonderful read!! I definitely liked every part of it and i also have you book-marked to look at new things on your website.
Comments are closed.